Apple as a company has always been tight-lipped. This is what gets the rumour mill to fever pitch just before their product announcements, and how they manage to get their products and services from announcement to launch within days rather than the months of their competitors. No-one inside or outside of Apple knows about upcoming products and services except those directly working on them. This is great for marketing purposes and staying ahead on the competition in product development, but it is far from useful when you are facing large-scale security issues.
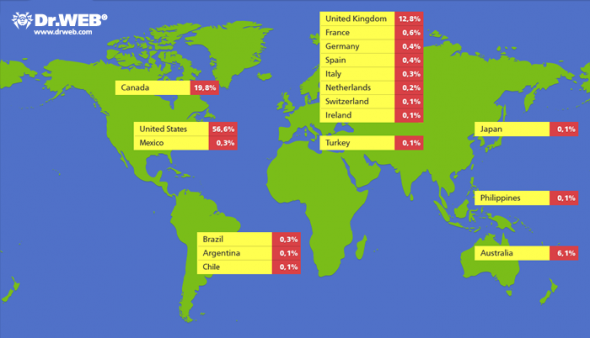
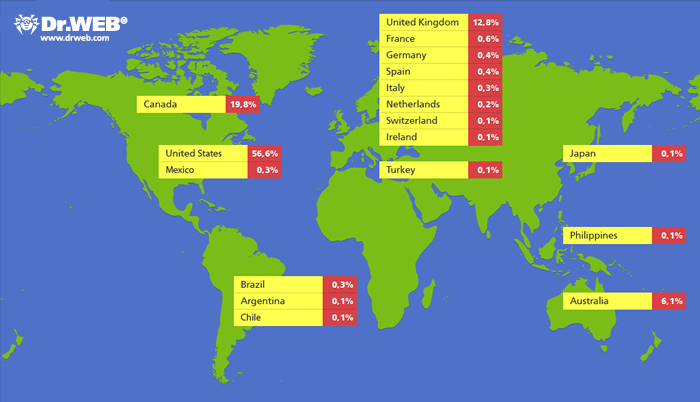
The internet lit-up last week with the news that their was 550,000-strong botnet created of infected Apple computers running OSX – mostly MacBooks, MacBook Pros, and MacBook Airs. Apple had previously escaped the same security issues faced by Microsoft, and whilst Apple fanboys would say their system is more secure, it has always been more the case that Apple had security through obscurity more than and actually better security than Windows 7. There are simply a multitude more computers running Windows than OSX, and so hackers and botnet creators would target Windows machines.
Recently, as Apple is selling more computers than their competitors, OSX has become a more relevant target to hackers, and as we saw from the news from security experts Dr Web last week – we now have a large-scale problem of infection with the Flashback botnet. The infection was made through a security hole in Java, as has often been the case on Windows machines – but that does not reduce the scale of the issue. Apple, then, needed to deal with outside security experts for the first time in order to get a handle on the problem – except as is with the case with Apple, they don’t work well with others.
In fact, whilst Dr Web were the people to raise the alarm about this botnet, and had created a botnet “sinkhole” with a spoofed command and control centre for the botnet – Apple tried to get Dr Web’s servers taken offline by contacting their registrar Reggi.ru. Yes Dr Web did have control of much of this botnet, but that is only because they had managed to catch it and spoof the addresses in an attempt to monitor and then fix the issue. But Apple did not reach out to them about this, they remained publicly silent on the issue and tried to shut them down.
In its defence, Apple may not have heard of Dr Web before their announcement on the Flashback botnet when they got in touch with Apple earlier this month. However, the botnet was confirmed by Kaspersky on Friday, and Apple have still not spoken to Dr Web about their findings or how they could help fix the situation. Kaspersky have said that Apple are working with the security industry now, and are attempting to shut down the heads of the hydra by taking down the controller domains – but this could and should have been done much earlier if Apple didn;t try and keep everything behind closed doors. In fact, the security patch through which Apple users got the infection was patched by Oracle in February but not fixed by Apple until earlier this month – a very slack treatment of the security of its users. And now nearly 1% of Apple’s userbase is infected.
This is, however, sadly another tier to the problems Apple faces when the company is simply trying to keep everything in-house – a policy which works when it is a small visionary company, but not so well when it is the biggest company in the world.
[via Forbes]

Pingback: Uhoh, New Java Exploit Found For Apple Mac OSX | TechFruit